Social engineering remains a common tool in cybercriminals’ arsenal in the rapidly evolving landscape of attack vectors for users and organizations. While phishing attacks have garnered significant attention, various other deceptive tactics are employed by cybercriminals. Organizations tend to believe that social engineering is just conducting simulated phishing tests to increase end users’ understanding of spotting the tell-tale signs of a phishing email. It is essential for end users to go through a series of questions, checks, and pauses to ensure end users are not falling victim to phishing attacks.
However, social engineering involves other facets and capabilities that, while used in phishing, are also done with QR codes, USB flash drives, phone calls, in-person, and text messages via SMS or social media.
Impersonation: The Art of Deception
Impersonation is a tactic that preys on human trust and vulnerability, with attackers masquerading as someone else to extract sensitive information or gain unauthorized access. One well-known case using impersonation over the phone through vishing was the Twitter Bitcoin scam. In this scam, two teenagers working with other accomplices gained access to several high-profile Twitter accounts, including those of Elon Musk, Bill Gates, and Barack Obama. They impersonated the account owners and posted tweets asking followers to send $1,000 in cryptocurrency to a specified address, promising to double the amount but only within a short time. One hundred and eighteen users fell victim to the scam, giving the thieves $118,000 in less than 30 minutes.
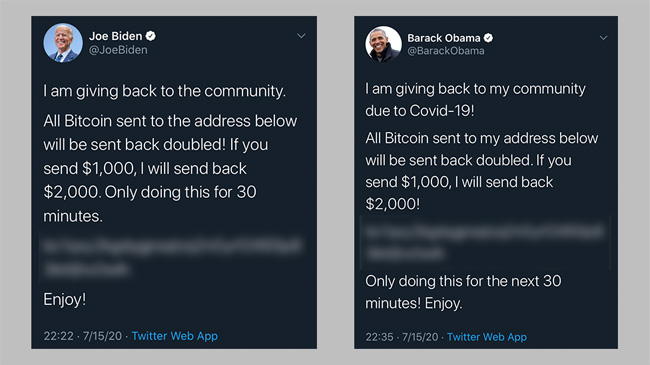
Figure 1: Source:https://ichef.bbci.co.uk/news/640/cpsprodpb/149E4/production/_113425448_chris-nc.png
Luckily, the thieves were caught the following week when they tried to exchange their bitcoin to hard currency, where authorities were waiting for them at the financial institution.
When protecting against impersonation attacks, taking the time to verify their identity is the first step, followed by gaining information about them to verify, like phone numbers, email addresses or their names. This information can then be cross referenced to ensure their identity. From a technology standpoint, implementing Multifactor Authentication (MFA) on accounts can reduce the risk of successful unauthorized access, all of which is supported by the need for security awareness and training.
Pretexting: Crafted Narratives That Lure You In
Along with impersonation, pretexting is the action of creating a false scenario to deceive individuals and obtain sensitive information or unauthorized access. Attackers skillfully craft narratives, often posing as co-workers, authority figures, or even tech support personnel, to exploit human emotions like trust and compassion. Sometimes these start out easy with an email that appears to be from your CEO or manager asking if you are in the office today. Users are trained to watch out for links or unusual requests, whereas this one starts innocently. If the user responds, this initiates the demand for the victim to carry out an immediate appeal, and the sender is only available via email and restricts the opportunity to verify the request. The following action is to obtain gift cards for a client, guest, or someone of importance to be delivered as a token of appreciation. If the user responds and carries out the action, they fall victim to losing money as the request is for them to deliver the codes, not the actual cards, to the attackers, and once turned over, they have no way to get their money back if they discover it is a scam.
To protect against pretexting, it is always good to have a healthy level of skepticism, so we only sometimes believe everything on the internet. This consideration needs to expand to our emails as well. It is essential to be cautious when asked for sensitive information or simple requests and work to verify the person through secondary channels.
Baiting: The Temptation That Reels You In
Baiting is a social engineering tactic that plays on human curiosity and desire for immediate gratification. Attackers leave behind physical or digital “bait,” such as infected USB drives disguised as promotional giveaways, enticing unsuspecting individuals to take the bait. Once the malware-infected device is plugged in, it compromises the victim’s system. Social engineers have been known to drop USB drives in the physical area surrounding the target labeled “Executive Salary Information” or an executive’s name. The curious employees who pick up these drives and insert them into their computers may unknowingly expose their systems to malware.

Some organizations have taken precautions against this and are training users to protect against these attacks and provide procedures for users if they discover a USB drive in the surrounding area.
As technology evolves, so do the cybercriminals. They have advanced to using the popular QR codes found around in restaurants, retail locations and commercials. Cybercriminals will use QR codes on parking meters, signs advertising free merchandise, or restaurant specials, all to get users to scan the code and visit their website to launch malware or steal data. With QR codes, it is always good to verify what website is expected to be seen when the scan occurs. If it differs or the source is not well known or trusted, then do not scan it and instead do a Google search for the item.
To protect against baiting, it is essential to exercise caution with any physical media, especially if you do not trust the source and ones found in public. Turn them into security, or if you are technically minded, you can connect it to a sandbox or burner laptop that you do not mind wiping afterward to avoid the loading of malware or other attacks designed to infiltrate the system.
Armor Yourself Against Social Engineering Attacks
Users and organizations must stay vigilant and arm themselves with knowledge and proactive measures. By understanding the various tactics social engineering cybercriminals use, they can spot the multiple tactics and report them to the necessary people or groups.
To protect against social engineering attacks, users and organizations can implement all or some of the following:
- Educate and raise awareness: Train individuals to recognize and report social engineering attempts, fostering a security-conscious culture.
- Implement multifactor authentication: Utilizing multifactor authentication provides an additional layer of security to prevent unauthorized access.
- Employ strict access controls: Establish and enforce access control policies by deploying ID badges, access cards, or biometric systems.
- Maintain robust security solutions: Regularly update and maintain antivirus software and security solutions to detect and mitigate potential threats.
- Promote an empowering reporting culture: Encourage employees to report suspicious behavior and incidents to enable swift response and prevention.
Organizations and individuals must remain watchful and assertive as cybercriminals grow more sophisticated in their social engineering tactics. By cultivating a security-focused culture through ongoing education and enforcing solid technical controls, end users can be empowered to identify and resist the latest tricks. While no security solution is 100% secure and will not eliminate the threat of deception, awareness of cybercriminal techniques and critical thinking provides the human firewall and last line of defense for stronger security. Our ultimate defense is a combination of security-minded users and robust cybersecurity protections. United, they can collectively overcome the onslaught of social engineering.
September 7, 2023
James McQuiggan is a Security Awareness Advocate for KnowBe4. Prior to joining KnowBe4, McQuiggan worked for Siemens for eighteen years where he was responsible for various roles, including his most recent as Product & Solution Security Officer for Siemens Gamesa Renewable Energy. In this role, he consulted and supported various corporate divisions on cybersecurity standards, information security awareness and securing product networks. In addition to his work at Siemens, McQuiggan is also a part-time faculty professor at Valencia College in the Engineering, Computer Programming & Technology Division.
James is a CISSP and within the central Florida community, he is the President of the Central Florida (ISC)2 Chapter where he supports cybersecurity professionals with education and networking opportunities. Working with the Center for Cyber Safety and Education, he has taught the Safe and Secure Online education and awareness program to over 7,000 students, parents, teachers and the “life-experienced” (seniors) to ensure they understand the dangers of the internet. McQuiggan holds the SACP certification.

